Outline
Computer network
HTTP
HTTPS
UDP/TCP
Proxy
ports and IP
nmap
Scan IP in selected scope
Scan IP randomly
Scan DNS address
Scan IP only
Scan UDP Service only
Check specific ports' status
Load scripts
Zenmap GUI
Nmap Cheat Sheet
Burp Suite
Practice
nmap practice
brup practice
google hacking practice
firece & thehavester learning
SQLmap learning
netcat learning
Vulnerability Knowledge
Unsecure mechanism
Login; Logout; CAPTCHA ; Directory; Local File Vulnerability; Remote file Vulnerability ; File Inclusion Vulnerability
Session Management Testing
HTTP Only scenario; Secure Cookies; Session Fixation; CSRF; Bypass anti-CSRF;
Input Validation Testing
CSS Attacks
- Reflected
- Stored
- DOM-based
SQL injection
In-band SQL injection
Error-based
Union-based
Blind SQL injection
Boolean-based
Time-based
Out-of-band (OOB) SQL injection
Automation
- Commix
Command Injection
XML/XPATH Injection
PHP Code Injection
CVE/CWE Cases
Druppal SQL injection CVE-2014-3704
SQLite Manager File Inclusion CVE-2007-1232
SQLite Manager XSS CVE-2012-5105
Heartbleed CVE-2014-0160
HTML5 Insecure local storage CWE-922
ShellShock CVE-2014-6271
OWASP

MS-SDL
https://www.microsoft.com/en-us/securityengineering/sdl/practices
Pen-testing
Mobile Testing
MobSF learning/code reading
Pithos
Frida
iOS Jailbreak knowledge
Android smali scirpt editing
iOS client-side server CA
android client-side server CA
Bypass proxy CA issue
Hacking
Generate payload using metasploit
OWASP Mobile 10
- M1: Improper Platform Usage
- M2: Insecure Data Storage
- M3: Insecure Communication
- M4: Insecure Authentication
- M5: Insufficient Cryptography
- M6: Insecure Authorization
- M7: Client Code Quality
- M8: Code Tampering
- M9: Reverse Engineering
- M10: Extraneous Functionality
SSDLC
Development lifecycle
Requirement -> Architecture -> Test Planning -> Coding -> Testing(CICD)-> Release
SSDLC Framework
NIST 800-64
MS SDL
Provide Training
Define Security Requirements
Define Metrics and Compliance Reporting
Perform Threat Modeling (e.g. STRIDE)
Threat Desired property Spoofing Authenticity Tampering Integrity Repudiation Non-repudiability Information disclosure Confidentiality Denial of Service Availability Elevation of Privilege Authorization Establish Design Requirements
Define and Use Cryptography Standards
Risk of 3-rd Components Management
Use approved tools
Static Security Testing (SAST)
Dynamic Security Testing (DAST)
Penetration testing
Establish Standard Incident Response Process
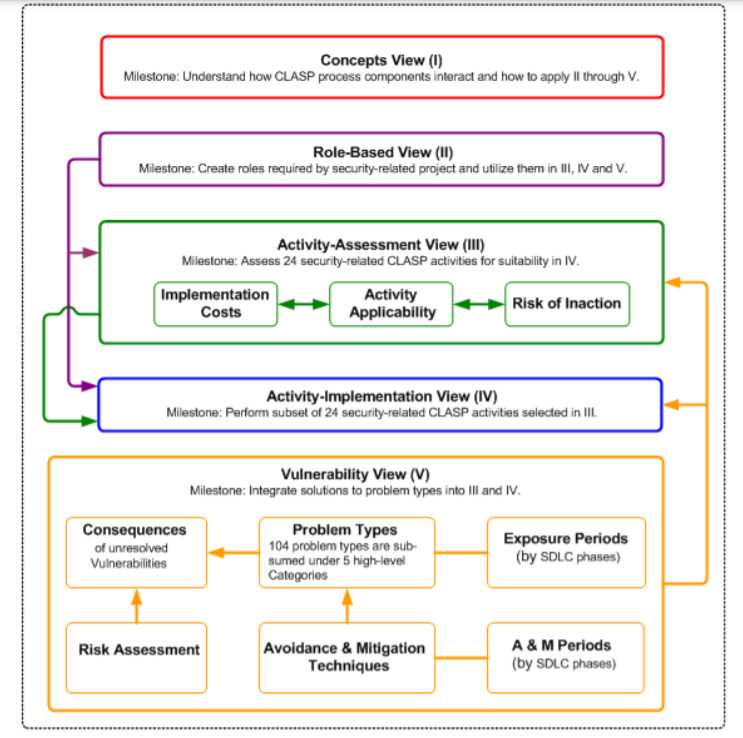
OWASP CLASP
Anti-Sql injection in development
Anti-XSS
Anti-CSRF
Anti-Code injection
- XPath
- Json